Smartphone It’s crucial to understand that in today’s digital age, cyber criminals can exploit your smartphone and eavesdrop on your conversations without your knowledge. This puts your privacy and sensitive information at risk. Taking proactive measures to protect your device and prevent unauthorized access is essential in safeguarding your personal information.
1. It’s important to keep your phone updated to ensure it has the latest security patches and features.
Keeping your phone updated is crucial in order to have the most current security patches and features. This is essential for protecting your personal information from potential cyber threats and ensuring that your phone functions at its optimal level. It’s a straightforward process that can greatly enhance the security and performance of your device.
Smartphone It’s important to regularly update your phone to ensure it has the latest security patches and features. These updates help protect your personal data from potential security threats and can also improve the performance and functionality of your device. Make sure to regularly check for and install any available updates for your phone.

Frequent security patches are issued to address potential vulnerabilities that hackers could exploit, while software updates often include new features and improvements to enhance your device’s performance and user experience. Keeping your phone regularly updated ensures it remains secure and up to date with the latest technological advancements.
2. Using strong and unique passwords for all your accounts can help prevent unauthorized access.
It is important to use strong and unique passwords for all of your accounts in order to prevent unauthorized access. This involves using a combination of uppercase and lowercase letters, numbers, and special characters. It is also important to avoid easily guessable passwords such as “password” or “123456.” By creating unique passwords for each account, you can significantly decrease the risk of unauthorized individuals gaining access to your personal information.
Smartphone Using weak passwords can make it easier for hackers to gain access to your personal information and compromise your security. To protect yourself, it’s important to create strong and unique passwords that include a combination of letters, numbers, and special characters. Smartphone Avoid using easily guessable information and take steps to lower the risk of unauthorized access, in order to safeguard your sensitive data.
I It is crucial to use strong and unique passwords for all of your accounts in order to prevent unauthorized access. This means incorporating a combination of uppercase and lowercase letters, numbers, and special characters to create a password that is difficult to guess.Smartphone It is also important to use a different password for each account to minimize the risk of a security breach. By following these guidelines, you can greatly decrease the chances of unauthorized access to your personal and sensitive information.
3. Installing anti-malware and security apps on your devices can provide an extra layer of protection against cyber threats.
Smartphone It is important to install anti-malware and security apps on your devices in order to add an extra layer of protection against cyber threats. These apps are designed to detect and remove malicious software, protect your personal information, and prevent unauthorized access to your devices. It is crucial to regularly update these apps to ensure that you are protected against the latest cyber threats.

By installing anti-malware and security apps on your devices, you can add an extra layer of protection against cyber threats. SmartphoneThese apps can detect and remove malicious software, safeguard your personal information, and block unauthorized access to your devices. It’s crucial to consistently update and run scans with these apps to ensure your devices are always safeguarded.
4. When using public Wi-Fi, be cautious of potential security risks and consider using a virtual private network (VPN) for added security.
It is crucial to exercise caution when using public Wi-Fi due to potential security risks. Hackers have the ability to intercept data on public networks, which can put your personal information at risk. One effective method to enhance security is by using a virtual private network (VPN). By encrypting your internet connection, a VPN provides an added layer of protection and safeguards your data from potential threats. Utilizing a VPN is a simple and effective way to ensure safety while using public Wi-Fi.
Smartphone When using public Wi-Fi, it’s important to be cautious due to security risks. Hackers can exploit your personal information on these networks, so it’s best to avoid accessing sensitive data like online banking or personal emails. Using a virtual private network (VPN) can add an extra layer of security by encrypting your internet connection and providing a secure and private browsing experience, ultimately protecting your data from potential threats on public Wi-Fi networks.
One way to increase your security is by using a virtual private network (VPN). A VPN encrypts your internet connection, making it more difficult for hackers to access your data. This added layer of security can help safeguard your personal information and sensitive data while using public Wi-Fi.
5. Reviewing app permissions on your devices can help you control what data and features each app can access.
Smartphone It is important to pay attention to the permissions we grant to the apps on our devices as technology becomes increasingly integrated into our daily lives. By carefully reviewing app permissions, we can have greater control over the data and features that each app can access. Smartphone This can help protect our privacy and security, and ensure that we only share information that we are comfortable with. Taking the time to review and adjust app permissions is a simple but effective way to manage our digital privacy.
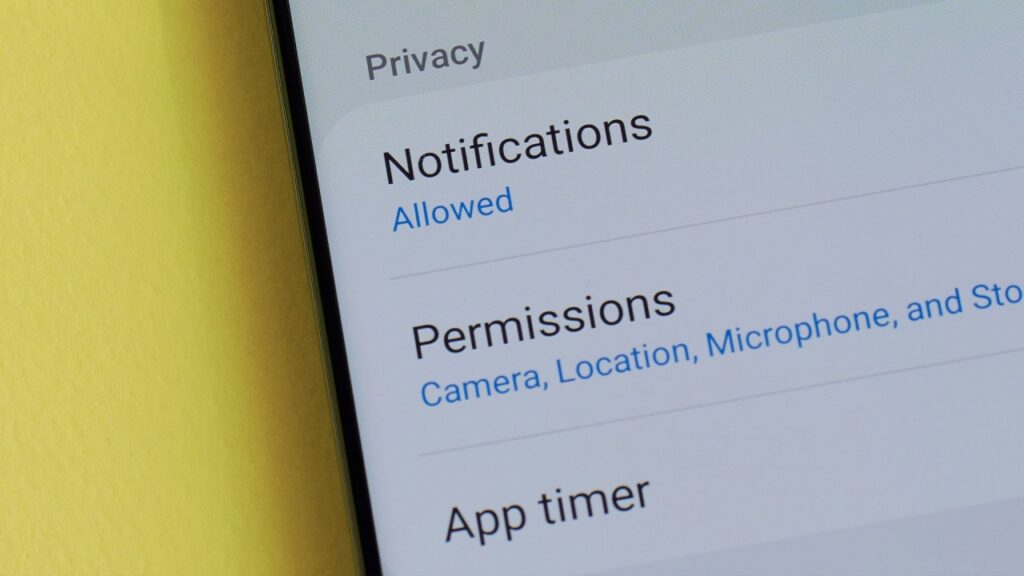
Reviewing app permissions is essential for controlling what data and features each app can access on your devices. By taking the time to review and adjust these permissions, you can protect your personal information and ensure the security of your device functionality. SmartphoneThis is particularly important in today’s environment, where there are growing concerns about data privacy and security. It’s crucial to stay in control of your devices by regularly reviewing your app permissions and making any necessary adjustments.
6. Be cautious of phishing attempts, which are often disguised as legitimate messages or websites aiming to steal your personal information.
Smartphone Phishing attempts are frequently employed by cyber criminals to obtain personal information. These deceptive tactics often involve posing as legitimate messages or websites in order to deceive individuals into divulging sensitive data like passwords or financial information. It is crucial to exercise caution and refrain from clicking on suspicious links or sharing personal information unless you can verify the authenticity of the source. Always take the time to confirm the sender or website before proceeding.
Smartphone Frequently, scammers disguise themselves as legitimate messages or websites to deceive individuals into sharing sensitive information such as passwords, social security numbers, or credit card details. It is extremely important to be cautious and sceptical when receiving unsolicited messages or visiting unfamiliar websites that ask for personal information. Always make sure to verify the authenticity of the request before disclosing any sensitive data.
7. Enabling two-factor authentication adds an extra layer of security by requiring a second form of verification to access your accounts.
Enabling two-factor authentication provides an additional level of security by necessitating a second form of verification to access your accounts. This means that even if someone obtains your password, they will be unable to access your accounts without that second form of verification.Smartphone It is a crucial measure in safeguarding your online accounts from unauthorized access and potential security breaches.

Utilizing two-factor authentication significantly boosts the security of your accounts by requiring an additional form of verification, such as a one-time code sent to your phone, a fingerprint scan, or a physical security key. This is an essential step in protecting your sensitive information and thwarting unauthorized access to your accounts.
8. Avoid clicking on suspicious links in emails, messages, or websites to protect yourself from potential malware or phishing attacks.
It is crucial to prioritize your safety from malware and phishing attacks by refraining from clicking on any suspicious links in emails, messages, or websites. These links may result in the installation of harmful software on your device or could be used to steal your personal information.Smartphone It is advisable to exercise caution and refrain from clicking on any links that appear suspicious or out of the ordinary. By taking this simple step, you can effectively shield your personal information and devices from cyber threats.
Smartphone It is important to be cautious when interacting with emails, messages, or websites that contain suspicious links. These links can pose a risk of malware or phishing attacks, potentially compromising your personal information. To protect yourself, it is best to avoid clicking on any links that seem suspicious or unfamiliar. It is advisable to verify the source and legitimacy of a link before clicking on it to ensure your online safety.
9. Regularly backing up your data ensures that you have a copy of important information in case of a security breach or device failure.
Regularly backing up your data is crucial in order to protect your important information. SmartphoneIn the event of a security breach or device failure, having a copy of your data ensures that you can still access and recover your essential files. This precaution is important to safeguard against any unexpected loss of data.

It is important to regularly back up your data to protect your important information. By doing so, you can have a copy available in case of a security breach or device failure, which can help prevent loss of critical information and minimize the impact of any potential data loss.Smartphone Establishing a regular schedule for backing up your data ensures that you always have access to the latest versions of your files.
10. Staying informed about cybersecurity threats and trends can help you make informed decisions about protecting your personal and sensitive information.
Smartphone Staying informed about cybersecurity threats and trends is crucial for protecting your personal and sensitive information. By staying updated on the latest developments in cybersecurity, you can make informed decisions about the measures you need to take to safeguard your data. This includes being aware of common tactics used by cybercriminals and understanding the best practices for protecting yourself online. Keeping up with cybersecurity news and trends can help you stay one step ahead of potential threats and ensure that your information remains secure.

Smartphone In order to protect your personal and sensitive information, it is crucial to stay informed about cybersecurity threats and trends. By staying up to date on the latest developments, you can make informed decisions about the security measures you need to take to safeguard your data. Whether it’s keeping an eye on the latest malware threats or understanding the potential risks of using public Wi-Fi, staying informed is the key to staying safe in an increasingly digital world.
Interested in Reading My Article On:Groundbreaking AI techniques have earned the Nobel Prize for Physics winners.